
SSH Keys: A Complete Guide to Generation, Authentication & Security
An SSH key is a secure access credential used in the Secure Shell (SSH) protocol, leveraging public key infrastructure (PKI) technology for authentication and encryption. This authentication method is crucial for protecting cloud services, network environments, and file transfers.
SSH Key Pair Components
SSH keys consist of two parts:
- Private Key: A secret key known only to the user, encrypted and stored securely
- Public Key: Can be freely shared with SSH servers for connection purposes
These keys use strong algorithms like RSA (2048-bit) or ECDSA (521-bit) to generate secure, random numeric combinations.
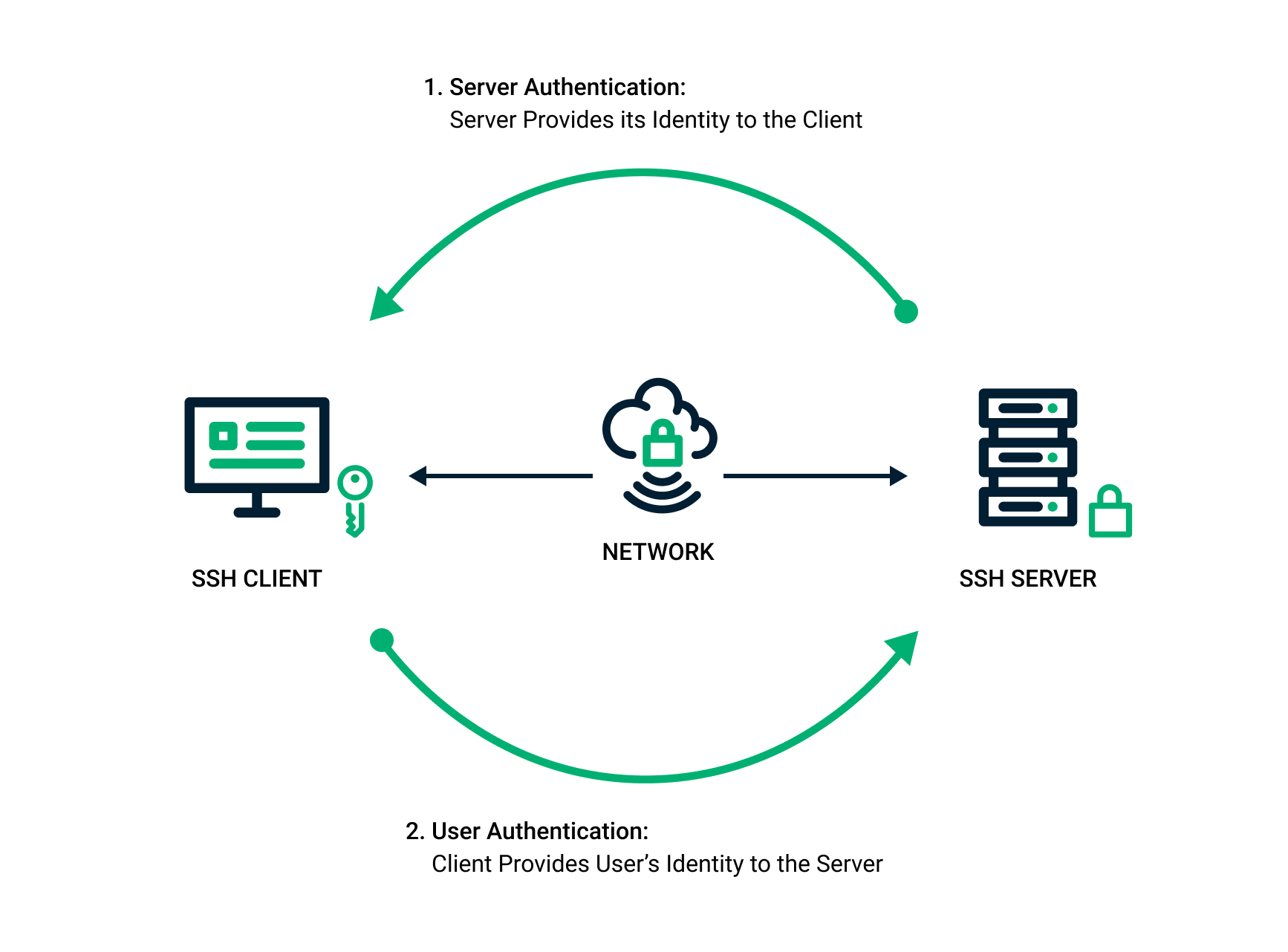
SSH client-server authentication process
Authentication Process
When connecting to a remote server:
- User requests connection via SSH client
- Server sends encrypted challenge using public key
- Client decrypts challenge with private key
- Server grants access after successful response
Advantages Over Passwords
SSH keys offer several benefits:
- Stronger security against brute force attacks
- Automatic authentication without manual entry
- Not vulnerable to common password theft methods
- Future-proof against evolving threats
Finding SSH Keys
Default locations:
- Linux/MacOS: ~/.ssh directory
- Windows: C:\Users<username>.ssh Look for files named id_dsa or id_rsa (private key) and their .pub counterparts (public key)
Generating SSH Keys
Basic steps to generate a key pair:
- Run ssh-keygen -t rsa
- Specify save location (usually ~/.ssh/id_rsa)
- Add optional passphrase
- Copy public key to remote server using ssh-copy-id
Configuration and Management
Configure SSH through:
- Server: /etc/ssh/sshdc_config
- Client: .ssh/config
Best practices for management:
- Implement proper provisioning and termination policies
- Use centralized certificate management
- Regularly audit and remove unused keys
- Protect private keys with passwords or hardware tokens

Tim Callan headshot in collared shirt
Related Articles

Transfer Fraud: Essential Tips to Protect Your Money from Scammers
